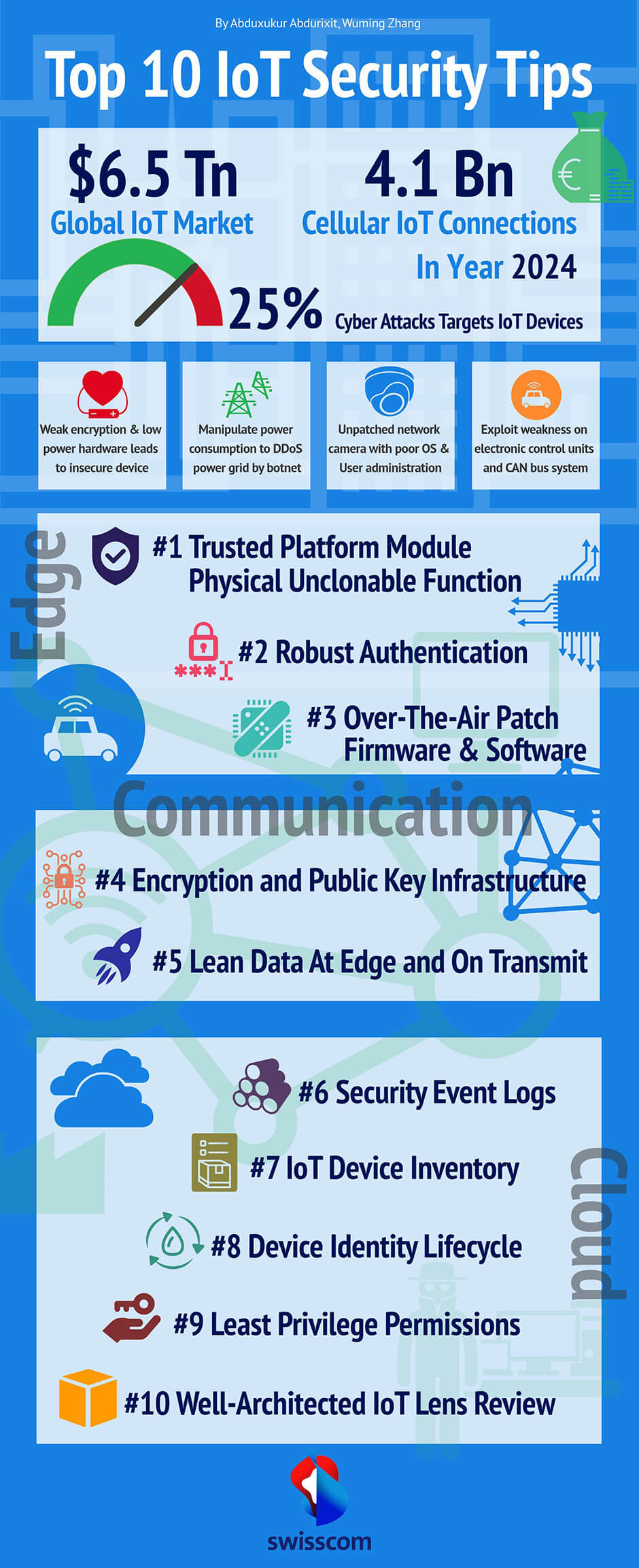
On the edge, regardless of the hardware. Use a trusted platform module or physically unclonable function to physically protect the device from tampering. Strong local authentication to avoid brute-force of the device. Software by nature will have bugs, therefore Over-The-Air upgrade or any sort of patch management is essential.
On communication, we need to guarantee the encryption for the data at rest and the data in transit. Working with digital certificates is a must. Use additional defense method on the network layer to detect unusual traffics. By doing lean data on edge, data will be difficult for the unlawful third party to interpret in a meaningful way. Enrich the data once arrives in the cloud.
In the cloud, we need to gather all security-related events from the edge devices and build up a warning system as a detective control. A proper IoT Device Inventory with Identity Lifecycle will help us to avoid the device fall into the wrong hands. Least privilege for each device and user allowed to do is critical to avoid any configuration error. Last but least, a continues well-architected review with IoT Lens of the whole system is always valuable and necessary to discover & measure and improve the overall IoT security and performance.
By 2024, 25% percent of the data we generate will be real-time, this means we have to get security right from the very beginning. This is a challenging task to apply across all business units. By following the security best practices and our top ten IoT security tips will help inform the overall IoT cybersecurity strategy and allow us to implement security measures across the business. No matter how extended it becomes!