Cloud Services
Take care of your AWS Access Keys
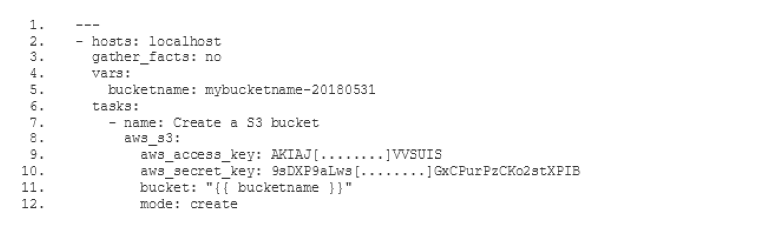
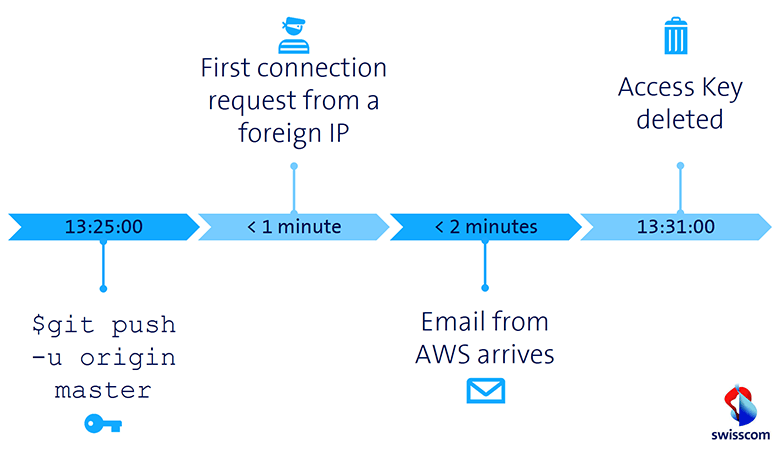
Identity and Access Management (IAM) is an important area within the Security Chapter of the Amazon Web Services' (AWS) Well-Architected Framework. Within Swisscom we share this opinion. To raise awareness and to deal with AWS technologies, we started a simple test. We wanted to find out what happens when valid AWS Access Keys are published on GitHub. This blogpost describes the procedure and the effects.