Managed NDRaaS
Ensure visibility with Network Detection & Response
Corporate networks are often hybrid and spread across several locations. When it comes to cyber defence, it is important to maintain a complete overview, and this includes complex networks.
With Network Detection & Response (NDR), you get the visibility back and can detect cyber attacks at an early stage.
When is it the right solution?
The network is an important component of cyber defence. Companies require a wide range of security mechanisms to detect and block cyber attacks. You therefore need a solution to analyse the network traffic and rapidly detect anomalies as well as potential vulnerabilities – for novel types of attack too.
The first step
Services in detail
Two service options are available. With the On-Premise version, the NDR appliance runs on your own infrastructure. With the Managed version, Swisscom operates the appliance in one of its own Swiss data centres.
- Static and dynamic detection of cyber threats using machine learning
- Detection and visualisation of cyber threats including in DNS traffic and through web proxies
- Graphic display of all devices in the network including internal shadow IT
- Support to operate the appliance
- Optional analysis and assessment of security alerts in combination with Security Analytics as a Service/SOCaaS
- Static and dynamic detection of cyber threats using machine learning
- Detection and visualisation of cyber threats including in DNS traffic and through web proxies
- Analysis and assessment of security alerts
- Logging platform to compile and evaluate log files from various sources
- Operation of appliance in Swisscom data centres
- Optional analysis and assessment of security alerts in combination with Security Analytics as a Service/SOCaaS
Application examples
Detection of covert data leaks
Use AI-enabled detection to identify advanced persistent threats (APTs) and automate certain steps in the threat hunting process.
Early ransomware detection
Identification of shadow IT
Visualisation of the current threat status
Implementation of security guidelines
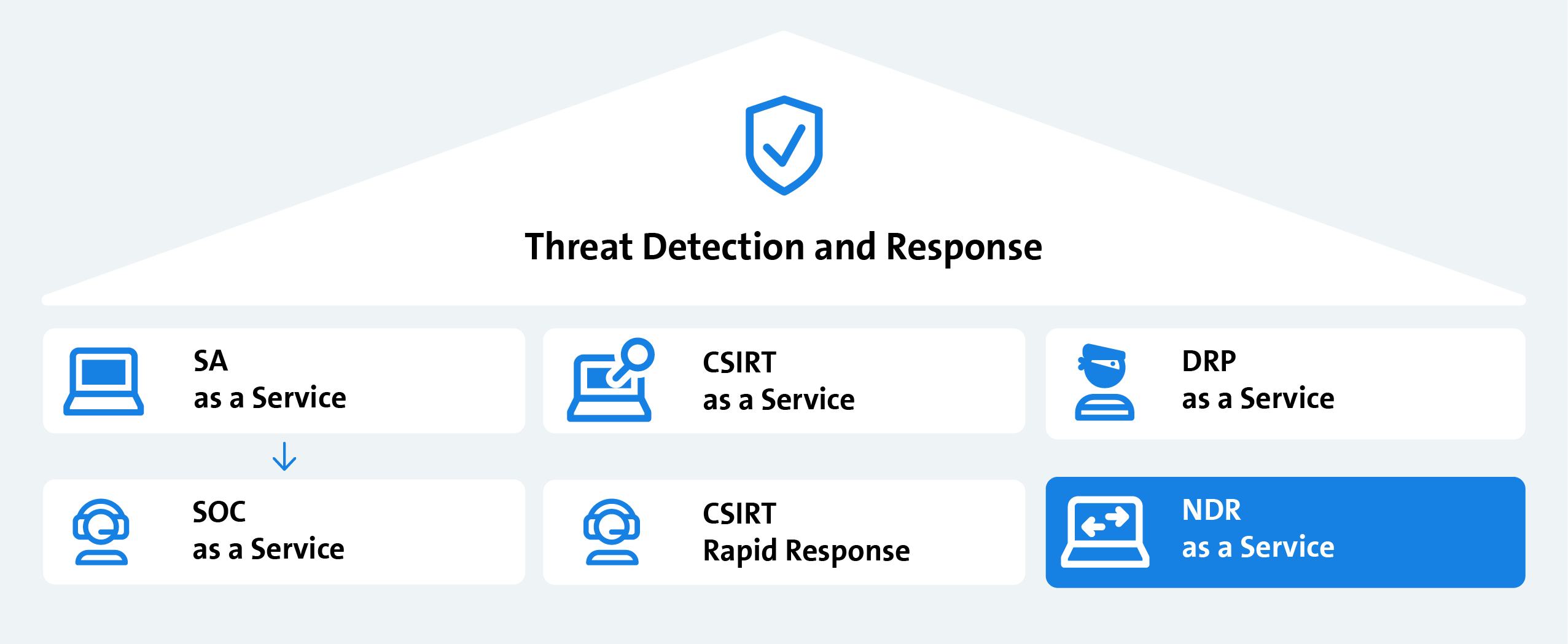
Network Detection & Response as part of the TDR portfolio
As an analytical module, NDRaaS complements the Threat Detection & Response service offerings. Detected threats can then be further processed via the services for analysis and incident response.